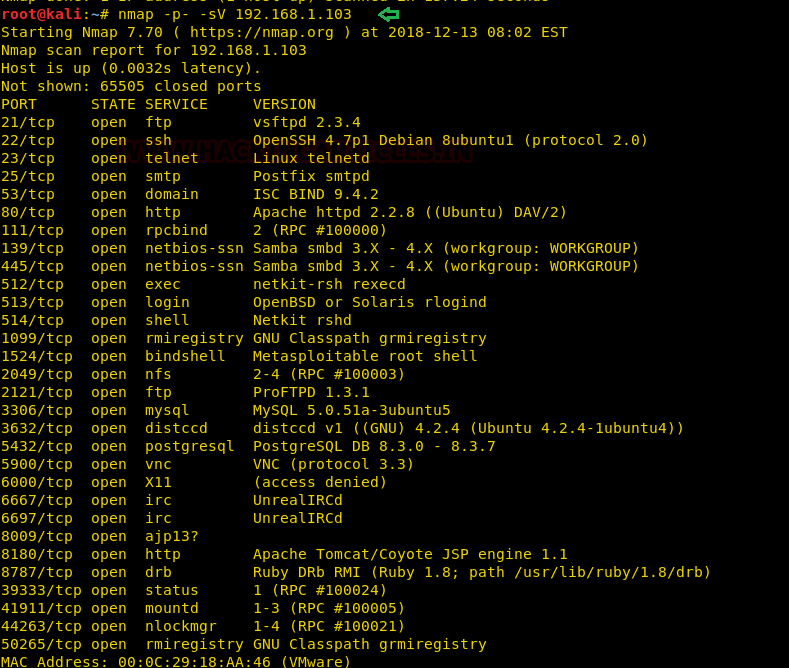
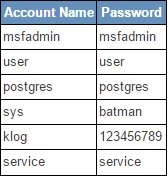
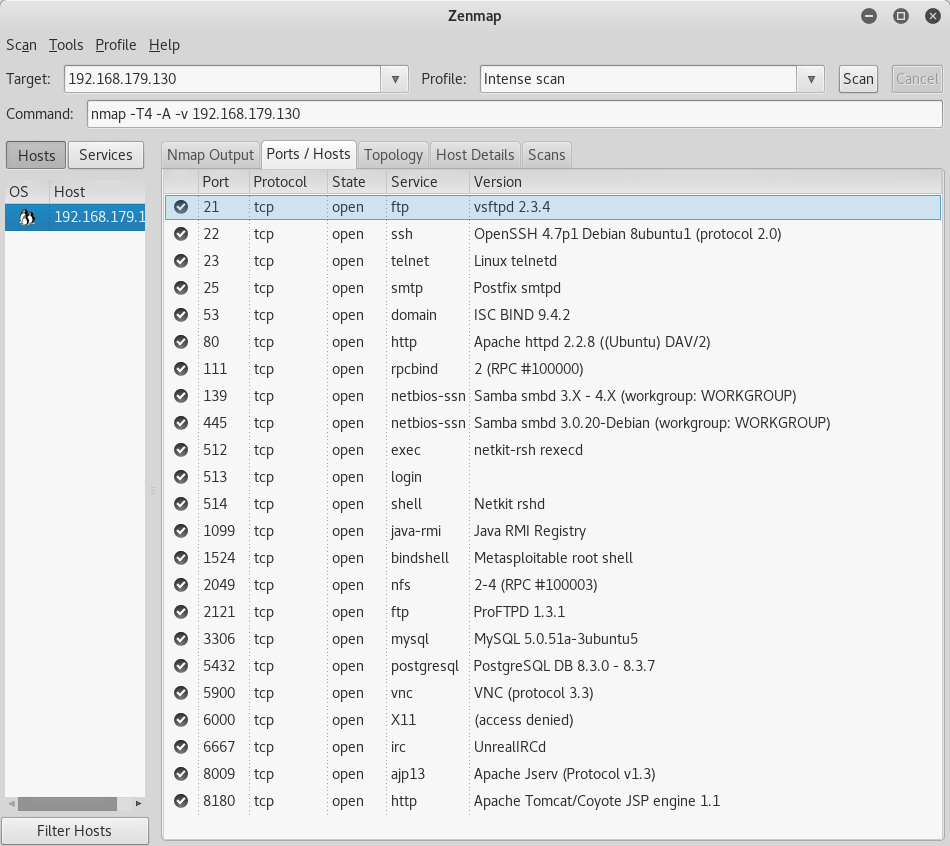
Metasploitable Login Credentials
Enter new unix password.

Metasploitable login credentials. Alternatively you can also use vmware workstation or vmware server. If the visudo command uses an unwanted editor you can use replacing nano by the editor you want to use. Once the vm is available on your desktop open the device and run it with vmware player. Metasploitable 2 has terrible password security for both system and database server accounts.
The primary administrative user msfadmin has a password matching the username. Metasploitable is an intentionally vulnerable linux virtual machine. Metasploitable3 is a vm that is built from the ground up with a large amount of security vulnerabilities. By discovering the list of users on this system either by using another flaw to capture the passwd file or by enumerating these.
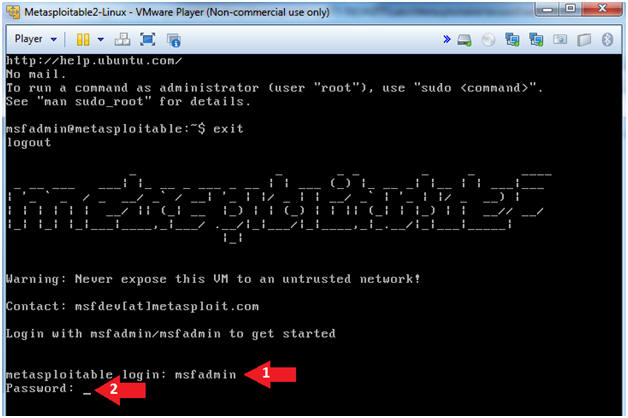
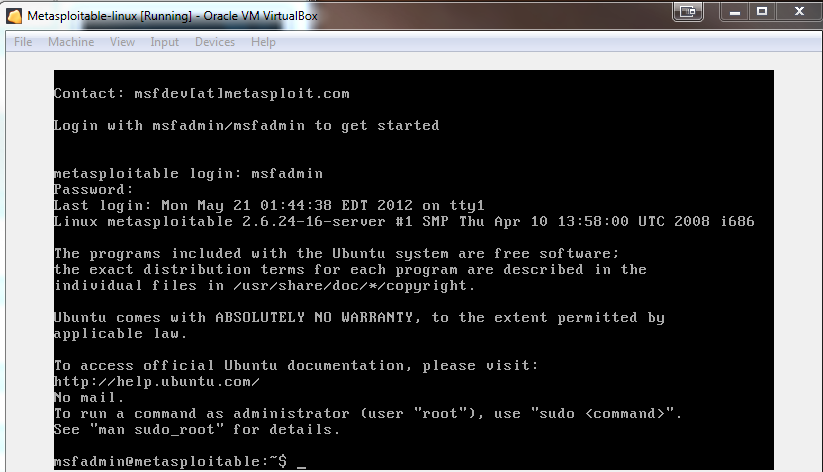
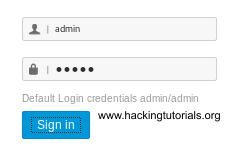
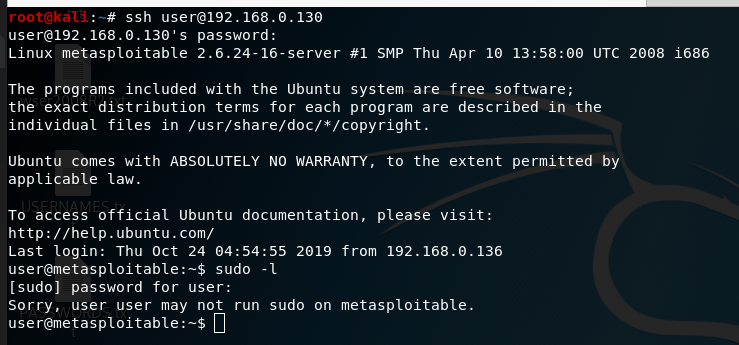
The login for metasploitable 2 is msfadminmsfadmin. Logging in to metasploitable 2. Disabling sudo password check. This is super easy to hack because the login screen for metasploitable gives the default username and password for in the etcissue file which we will change later.
This vm can be used to conduct security training test security tools and practice common penetration testing techniques. Download metasploitable 2 here first off the biggest issue with metasploitable is the passwords for the accounts. Exploiting mysql with metasploit. It is intended to be used as a target for testing exploits with metasploit.
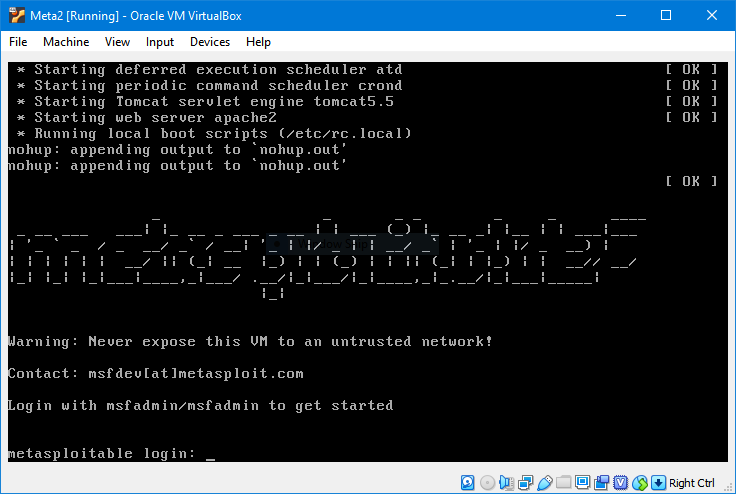
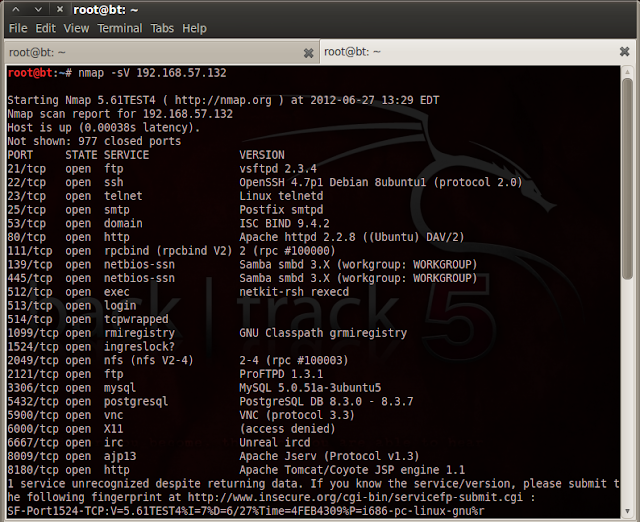
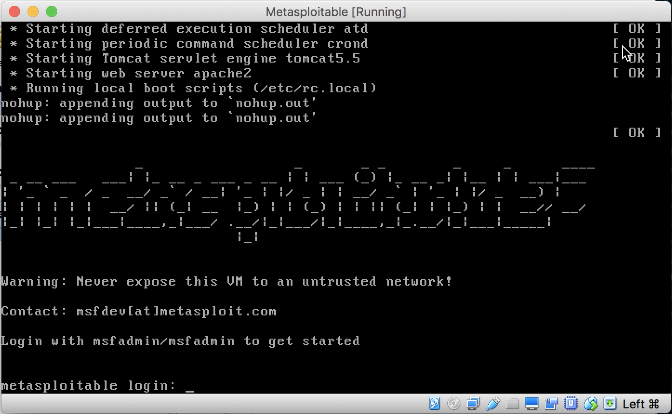
When metasploitable boots up the system prompts you for the metasploitable login. Identifying metasploitable 2s ip address. Supply same password change the root password. Metasploitable3 is released under a bsd style license.
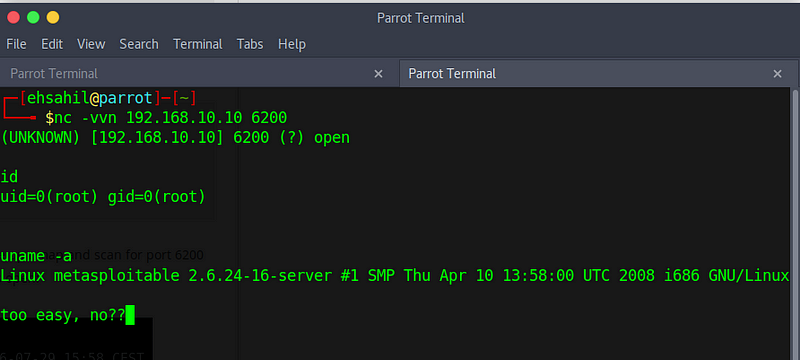
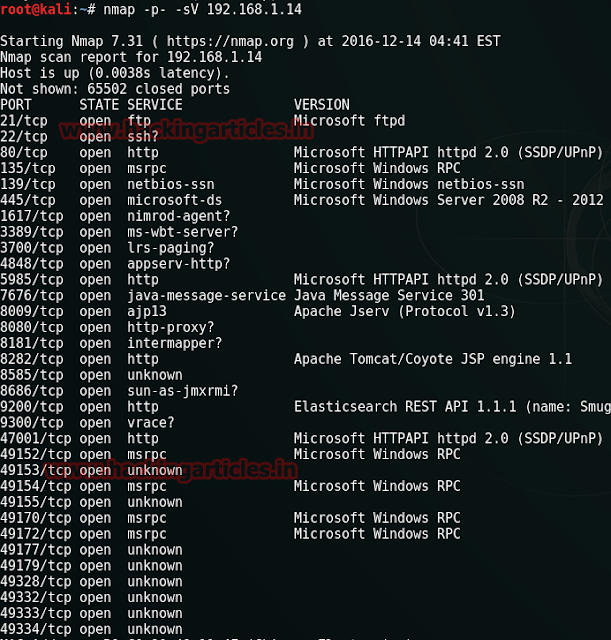
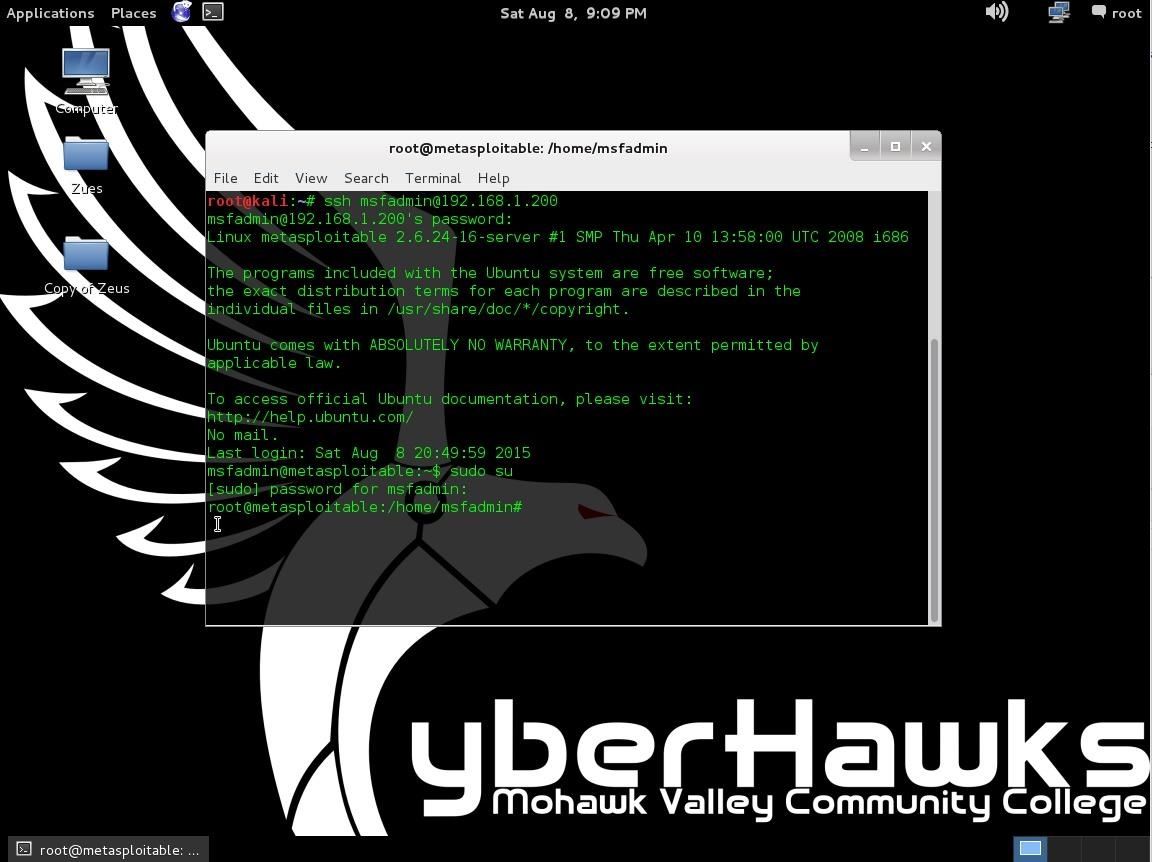
First off is to login with ssh and accept the key. Metasploitable is a virtual machine with baked in vulnerabilities designed to teach metasploitthis set of articles discusses the red teams tools and routes of attack. The following image shows the screen after you log in to metasploitable. To log in to metasploitable use the following credentials.
Metasploitablemysql exploiting postgresql with metasploit. Editornano sudo visudo 3. Supply new password retype new unix password. Setting user id to 0.
Powering on metasploitable 2.